Trucell Announced as Preferred Reseller of LG Diagnostic Displays in Australia
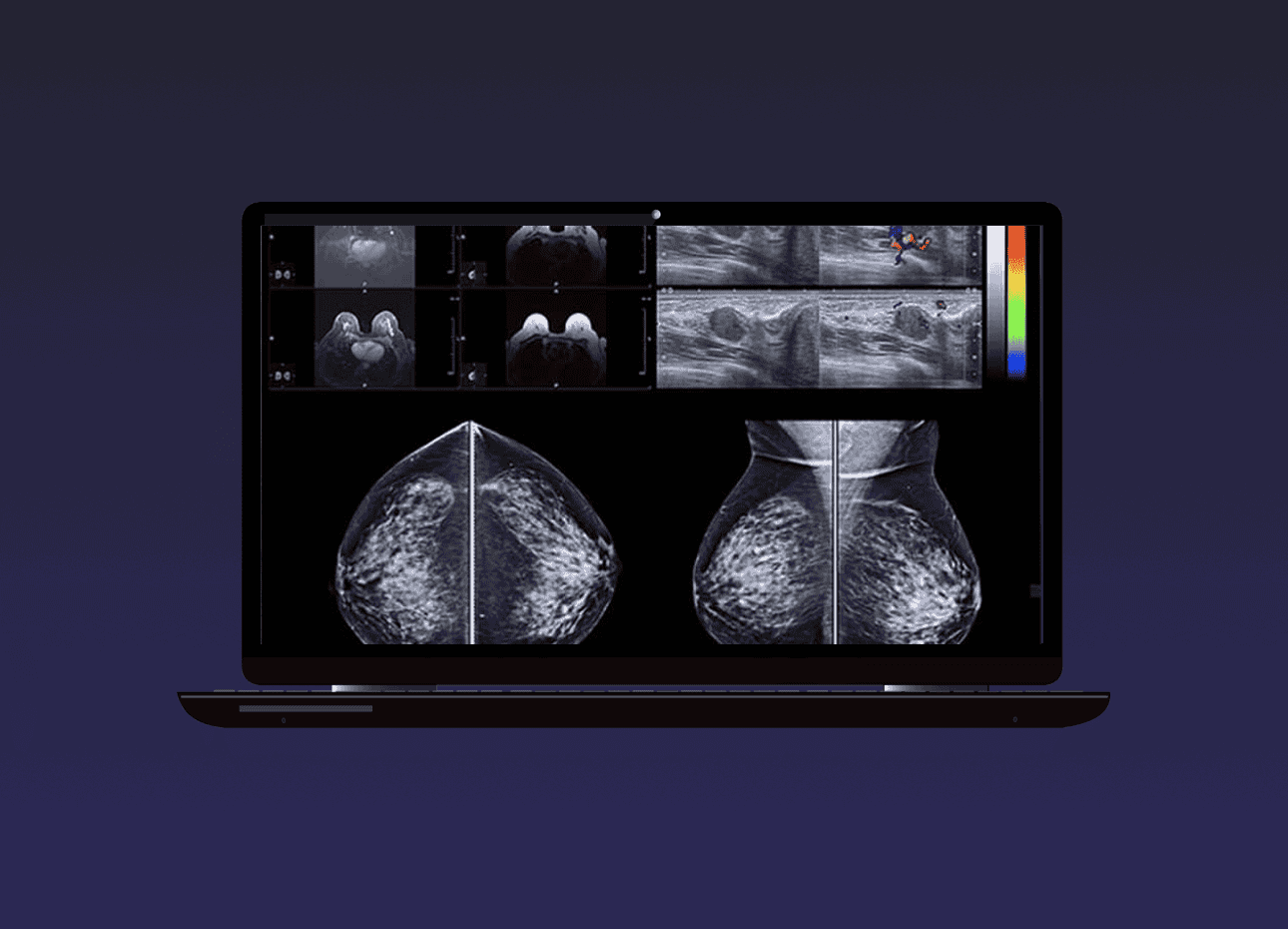
Trucell Pty Ltd, a leading provider of medical imaging solutions in Australia, is proud to announce that it has been selected by LG Electronics as one of its two preferred resellers for LG Diagnostic Displays in Australia. This partnership underscores Trucell’s commitment to providing the highest quality medical imaging technology to healthcare providers across the country. LG Electronics, a global leader in electronics and technology, has recognised Trucell’s dedication to excellence and customer service in the medical imaging sector. This partnership will allow Trucell to offer LG’s state-of-the-art diagnostic displays, known for their exceptional clarity, precision, and reliability, to a wider range of healthcare providers. LG Diagnostic Displays are designed to meet the demanding needs of today’s healthcare industry. They offer superior image quality, ensuring accurate diagnoses and patient treatment. With this partnership, Trucell will be able to provide these cutting-edge displays to hospitals, clinics, and medical centres across Australia.…